DoD Cybersecurity Compliance
IdenTrust ECA certificates can be used to access various secure agency websites, as well as for compliance with DoD Cybersecurity requirements to encrypt sensitive data and protect email communications from being compromised or viewed by unauthroized users. IdenTrust ECA certificates can be used to comply with these important requirements.
Use the resource links provided on this page to learn more about how IdenTrust ECA certificates are used to secure emailed communications.
Concepts
There are key concepts related to email security that is important to understand:
- A digital certificate includes a private key (which is never shared with anyone) and a public key (which is shared when signed or encrypted emails are exhanged).
- All email signing and encryption are managed by your email client.
- You must configure your ECA certificate in your email client in order to use email signing and encryption.
- In order to exchange encrypted emails, you and the recipient must both have a DoD-approved digital certificate, such as an IdenTrust ECA certificate or DoD CAC.
- A signed email can be used so that the recipient can be certain that you are the person who sent the email and that it has not been compromised in transit.
Let's explore these concepts further!
Configure Your Certificate
In order to use secure email functions, you must add your ECA certificate to your email client. Depending on your email client, you may also need to publish your digital certificate to the email Global Address List (GAL) which allows individuals within your organization to access your public key through your internal email directory and easily send you encrypted emails.
The following Illustration is based on the Microsoft Outlook configuration process and provides the key steps you will perform. To configure your certificate in email, choose the instructions for your email client provided in the links below:
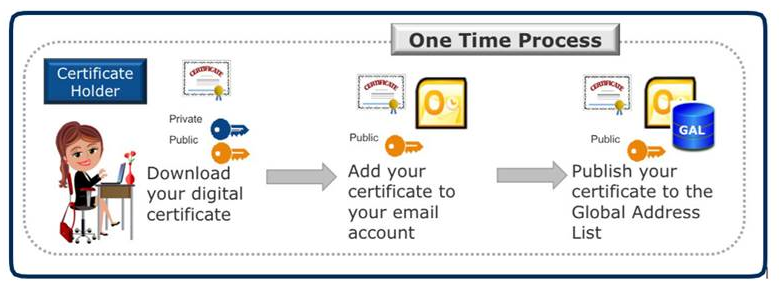
Exchange Certificate Public Keys
In order to exchange encrypted emails with your colleagues, you and each colleague must have a digital certificate and all of the certificates must be configured in the respective subscriber's email client through a simple process as described below. This process is a one-time configuration.
When an encrypted email is created, the public key of the intended recipient is used to encrypt the email contents. The encrypted email can only be unlocked by using the private key that was issued with the public key used for encryption. Because the recipient is the only one who has access to the private key, the recipient is the only one who can open and read the encrypted email.
The illustration below provides the key steps you and your colleagues will need to perform and is based on configuring Microsoft Outlook. If you need additional information about the email client you use, choose alternate email instructions provided in the Instructions for Configuring Secure Email section at the end of this page.
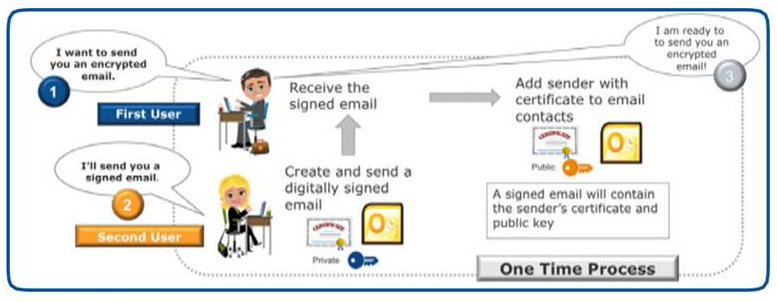
Start Using Secure Email
Once you and your colleagues have configured you email accounts, then you can begin exchanging secure emails. You can configure your email client to sign and encrypt all emails or you can turn on these settings when you originate and send an email. You might consider turning on email signing for all emails and only turn on encryption when you have a need to send a secure encrypted email.
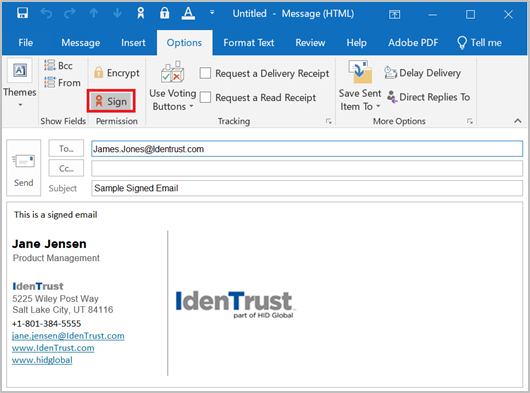
Signed Email
Microsoft Outlook Instructions are used to Illustrate these concepts below, however, you can select from the links provided below to view instructions for other email clients.
- Under the Options menu ensure that the Sign icon is selected. You can also select Encrypt, if you wish to Sign and Encrypt the email.
- Type your email and select the Send button.
- If you have set a password for your ECA certificate you may be prompted to authorize the use of the certificate or you may need to provide the password if one was set for your ECA certificate.
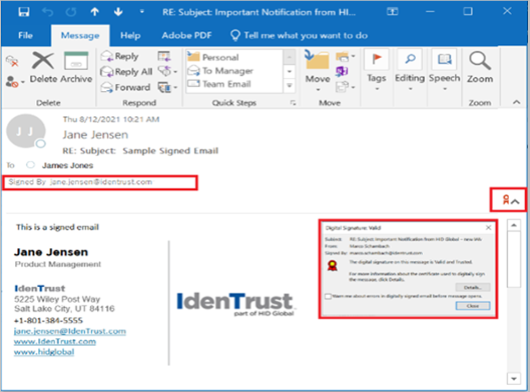
- When the recipient receives the signed email, it will have a signature icon in the email.
- The recipient can validate the digital signature by clicking on the signature icon.
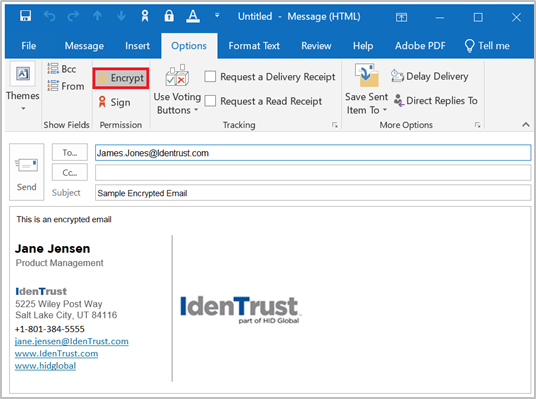
Encrypted Email
Microsoft Outlook is used to illustrate these concepts below; however, you can select from the links provided below to view instructions for other email clients.
- Under the Options menu ensure that the Encrypt icon is selected. You can also select Sign, if you wish to sign and encrypt the email.
- Type your email and select the Send button.
- You may be prompted to authorize the use of the certificate or you may need to provide the password if one was configured for your ECA certificate.
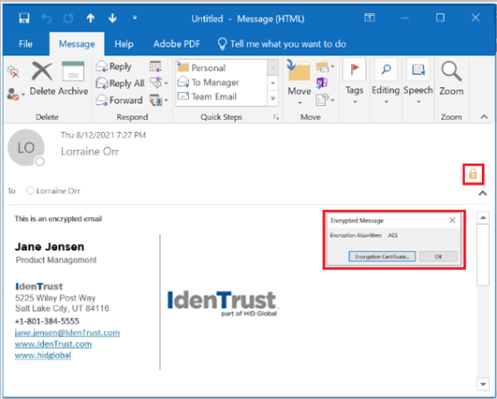
- When the recipient receives the encrypted email, it will have an encryption icon in the email.
- The recipient can click on the encryption icon to determine the method of encryption. The recipient can also click on the Encryption Certificate button to view the certificate that was used to encrypt the email.
Instructions for Configuring Secure Email
How to Set up Microsoft® Outlook to Sign and Encrypt Emails
How to Sign and Encrypt Emails in Microsoft 365®
How to Sign and Encrypt Emails in Microsoft® Outlook
How to Use a Digital Certificate in Apple Mail® to Digitally Sign and Encrypt Emails
How to Use a Digital Certificate in Lotus Notes® to Digitally Sign and Encrypt Emails
How to Use a Digital Certificate in Microsoft® Outlook for Mac to Digitally Sign and Encrypt Emails
How to Use a Digital Certificate in Mozilla® Thunderbird to Digitally Sign and Encrypt Emails
Please note that IdenTrust is in the process of updating these documents. Please contact us if you do not find what you need to configure your email client for secure email.
Other Resources
How to Add a Digital Certificate to Your Address Book
How to Add Sign and Encrypt Icons to Outlook Quick Access Toolbar

